Q. What is Active Directory?
Active Directory is the directory service
used by Windows 2000. A directory service is a centralized, hierarchical
database that contains information about users and resources on a
network. In Windows 2000, this database is called the Active Directory data store.
The Active Directory data store contains information about various
types of network objects, including printers, shared folders, user
accounts, groups, and computers. In a Windows 2000 domain, a read/write
copy of the Active Directory data store is physically located on each
domain controller in the domain.
Three primary purposes of Active Directory are:
- · To provide user logon and authentication services
- · To enable administrators to organize and manage user accounts groups, and network resources
- · To enable authorized users to easily locate network resources, regardless of where they are located on the network
A directory service consists of two parts—a
centralized, hierarchical database that contains information about users
and resources on a network, and a service that manages the database and
enables users of computers on the network to access the database. In
Windows 2008, the database is called the Active Directory data store, or
sometimes just the directory. The Active Directory data store contains
information about various types of network objects, including printers,
shared folders, user accounts, groups, and computers. Windows 2000
Server computers that have a copy of the Active Directory data store,
and that run Active Directory are called domain controllers. In
a Windows 2008 domain, a read/write copy of the Active Directory data
store is physically located on each domain controller in the domain.
Q. What are the physical components of active directory?
Logical Components of Active Directory
In creating the hierarchical database structure of
Active Directory, Microsoft facilitated locating resources such as
folders and printers by name rather than by physical location. These logical building blocks include domains, trees, forests, and OUs.
The physical location of objects within Active Directory is represented
by including all objects in a given location in its own site. Because a
domain is the basic unit on which Active Directory is built, the domain
is introduced first; followed by trees and forests (in which domains
are located); and then OUs, which are containers located within a
domain.
Domain:
A domain is a logical grouping of networked
computers in which one or more of the computers has one or more shared
resources, such as a shared folder or a shared printer, and in
which all of the computers share a common central domain directory
database that contains user account security information. One distinct
advantage of using a domain, particularly on a large network, is that
administration of user account security for the entire network can be
managed from a centralized location. In a domain, a user has only one
user account, which is stored in the domain directory database. This
user account enables the user to access shared resources (that the user
has permissions to access) located on any computer in the domain
Active Directory domains can hold millions of
objects, as opposed to the Windows NT domain structure, which was
limited to approximately 40,000 objects. As in previous versions of
Active Directory, the Active Directory database file (ntds.dit) defines
the domain. Each domain has its own ntds.dit file, which is stored on
(and replicated among) all domain controllers by a process called multimaster replication.
The domain controllers manage the configuration of domain security and
store the directory services database. This arrangement permits central
administration of domain account privileges, security, and network
resources. Networked devices and users belonging to a domain validate
with a domain controller at startup. All computers that refer to a
specific set of domain controllers make up the domain. In addition,
group accounts such as global groups and domain local groups are defined
on a domain-wide basis.
Trees
A tree is a group of domains that shares a
contiguous namespace. In other words, a tree consists of a parent domain
plus one or more sets of child domains whose name reflects that of a
parent. For example, a parent domain named examcram.com can include
child domains with names such as products.examcram.com,
sales.examcram.com, and manufacturing.examcram.com. Furthermore, the
tree structure can contain grandchild domains such as
america.sales.examcram.com or europe.sales.examcram.com, and so on, as
shown in Figure 1-2. A domain called que.com would not belong to the
same tree. Following the inverted tree concept originated by X.500, the
tree is structured with the parent domain at the top and child domains
beneath it. All domains in a tree are linked with two-way, transitive
trust relationships; in other words, accounts in any one domain can
access resources in another domain and vice versa.
![clip_image002[5] clip_image002[5]](http://winadmins.files.wordpress.com/2011/10/clip_image0025_thumb.jpg?w=282&h=190) Forests
Forests
A
forest is a grouping or hierarchical arrangement of one or
more separate, completely independent domain trees. As such, forests
have the following characteristics:
- All domains in a forest share a common schema.
- All domains in a forest share a common global catalog.
- All domains in a forest are linked by implicit two-way transitive trusts.
Trees in a forest have different naming structures, according to
their domains. Domains in a forest operate independently, but the forest
enables communication across the entire organization.
 Organizational Unit:
Organizational Unit:
An organizational unit (OU) is a container used to
organize objects within one domain into logical administrative groups.
An OU can contain objects such as user accounts, groups, computers,
printers, applications, shared folders, and other OUs from the same
domain. OUs are represented by a folder icon with a book inside. The
Domain Controllers OU is created by default when Active Directory is
installed to hold new Microsoft Windows Server 2003 domain controllers.
OUs can be added to other OUs to form a hierarchical structure; this
process is known as nesting OUs. Each domain has its own OU
structure—the OU structure within a domain is independent of the OU
structures of other domains.
There are three reasons for defining an OU:
-
To delegate administration – In the Windows Server
2003 operating system, you can delegate administration for the contents
of an OU (all users, computers, or resource objects in the OU) by
granting administrators specific permissions for an OU on the OU’s
access control list.
-
To administer Group Policy
-
To hide object
Physical Components of Active Directory
There are two physical components of Active Directory:
Domain Controllers
Any server on which you have installed Active Directory is a domain controller.
These servers authenticate all users logging on to the domain in which
they are located, and they also serve as centers from which you can
administer Active Directory in Windows Server 2008. A domain controller
stores a complete copy of all objects contained within the domain, plus
the schema and configuration information relevant to the forest in which
the domain is located. Unlike Windows NT, there are no primary or
backup domain controllers. Similar to Windows 2000 and Windows Server
2003, all domain controllers hold a master, editable copy of the Active
Directory database.
Every domain must have at least one DC. A domain may
have more than one DC; having more than one DC provides the following
benefits:
-
Fault tolerance: If one domain
controller goes down, another one is available to authenticate logon
requests and locate resources through the directory.
-
Load balancing: All domain
controllers within a site participate equally in domain activities, thus
spreading out the load over several servers. This configuration
optimizes the speed at which requests are serviced.
Sites
By contrast to the logical grouping of Active
Directory into forests, trees, domains, and OUs, Microsoft includes the
concept of sites to group together resources within a forest according
to their physical location and/or subnet. A site is a set of
one or more IP subnets, which are connected by a high-speed, always
available local area network (LAN) link. Figure 1-5 shows an example
with two sites, one located in Chicago and the other in New York. A site
can contain objects from more than one tree or domain within a single
forest, and individual trees and domains can encompass more than one
site. The use of sites enables you to control the replication of data
within the Active Directory database as well as to apply policies to all
users and computers or delegate administrative control to these objects
within a single physical location. In addition, sites enable users to
be authenticated by domain controllers in the same physical location
rather than a distant location as often as possible. You should
configure a single site for all work locations connected within a
high-speed, always available LAN link and designate additional sites for
locations separated from each other by a slower wide area network (WAN)
link. Using sites permits you to configure Active Directory replication
to take advantage
of the high-speed connection. It also enables users to connect to a domain controller using a reliable, high-speed connection.
![clip_image002[7] clip_image002[7]](http://winadmins.files.wordpress.com/2011/10/clip_image0027_thumb.jpg?w=324&h=120) Q. What are the components of Active Directory:
Object:
Q. What are the components of Active Directory:
Object:
An object is any specific item that can be cataloged in Active Directory. Examples of objects include users, computers, printers, folders, and files. These items are classified by a distinct set of characteristics, known as attributes. For example, a user can be characterized by the username, full name, telephone number, email address, and so on. Note that, in general, objects in the same container have the same types of attributes but are characterized by different values of these attributes. The Active Directory schema defines the extent of attributes that can be specified for any object.
Classes
The Active Directory service, in turn, classifies objects into classes. These classes are logical groupings of similar objects, such as users. Each class is a series of attributes that define the characteristics of the object.
Schemas
The schema is a set of rules that define the
classes of objects and their attributes that can be created in Active
Directory. It defines what attributes can be held by objects of various
types, which of the various classes can exist, and what object class can
be a parent of the current object class. For example, the User class
can contain user account objects and possess attributes such as
password, group membership, home folder, and so on.
When you first install Active Directory on a server, a
default schema is created, containing definitions of commonly used
objects and properties such as users, computers, and groups. This
default schema also contains definitions of objects and properties
needed for the functioning of Active Directory.
Global catalog
A global catalog server is a domain
controller that has an additional duty—it maintains a global catalog. A
global catalog is a master, searchable database that contains
information about every object in every domain in a forest. The global
catalog contains a complete replica of all objects in Active Directory
for its host domain, and contains a partial replica of all objects in
Active Directory for every other domain in the forest.
- A global catalog server performs two important functions:
- Provides group membership information during logon and authentication
- Helps users locate resources in Active Directory
Q. What are the protocols used by AD?
Because Active Directory is based on standard
directory access protocols, such as Lightweight Directory Access
Protocol (LDAP) version 3, and the Name Service Provider Interface
(NSPI), it can interoperate with other directory services employing
these protocols.
LDAP is the directory access protocol used to query
and retrieve information from Active Directory. Because it is an
industry-standard directory service protocol, programs can be developed
using LDAP to share Active Directory information with other directory
services that also support LDAP.
The NSPI protocol, which is used by Microsoft Exchange 4.0 and 5.x clients, is supported by Active Directory to provide compatibility with the Exchange directory.
Q. Minimum requirement to install Win 2008 AD?
- An NTFS partition with enough free space
- An Administrator’s username and password
- The correct operating system version
- A NIC
- Properly configured TCP/IP (IP address, subnet mask and – optional – default gateway)
- A network connection (to a hub or to another computer via a crossover cable)
- An operational DNS server (which can be installed on the DC itself)
- A Domain name that you want to use
Q. How do you verify whether the AD installation is proper?
-
Default containers: These are created automatically when the first domain is created. Open Active Directory Users and Computers, and then verify that the following containers are present: Computers, Users, and ForeignSecurityPrincipals.
-
Default domain controllers organizational unit: Open Active Directory Users and Computers, and then verify this organizational unit.
-
Default-First-Site-Name
-
Active Directory database: The Active Directory
database is your Ntds.dit file. Verify its existence in the
%Systemroot%\Ntds folder.
-
Global catalog server: The first domain controller becomes a global catalog server, by default. To verify this item:
-
a. Click Start, point to Programs, click Administrative Tools, and then click Active Directory Sites and Services.
-
b. Double-click Sites to expand it, expand Servers, and then select your domain controller.
-
c. Double-click the domain controller to expand the server contents.
-
d. Below the server, an NTDS Settings object is displayed. Right-click the object, and then click Properties.
-
e. On the General tab, you can observe a global catalog check box, which should be selected, by default.
Root domain: The forest root is created when the first domain controller is installed. Verify your computer network identification in My Computer.
The Domain Name System (DNS) suffix of your computer should match the
domain name that the domain controller belongs to. Also, ensure that
your computer registers the proper computer role. To verify this role,
use the net accounts command. The computer role should
say “primary” or “backup” depending on whether it is the first domain
controller in the domain.
Shared system volume: A Windows 2000
domain controller should have a shared system volume located in the
%Systemroot%\Sysvol\Sysvol folder. To verify this item, use the net share
command. The Active Directory also creates two standard policies during
the installation process: The Default Domain policy and the Default
Domain Controllers policy (located in the
%Systemroot%\Sysvol\Domain\Policies folder). These policies are
displayed as the following globally unique identifiers (GUIDs):
{31B2F340-016D-11D2-945F-00C04FB984F9} representing the Default Domain policy
{6AC1786C-016F-11D2-945F-00C04fB984F9} representing the Default Domain Controllers policy
SRV resource records: You must have a
DNS server installed and configured for Active Directory and the
associated client software to function correctly. Microsoft recommends
that you use Microsoft DNS server, which is supplied with Windows 2000
Server as your DNS server. However, Microsoft DNS server is not
required. The DNS server that you use must support the Service Resource
Record (SRV RR) Requests for Comments (RFC) 2052, and the dynamic update
protocol (RFC 2136). Use the DNS Manager Microsoft Management Console
(MMC) snap-in to verify that the appropriate zones and resource records
are created for each DNS zone. Active Directory creates its SRV RRs in
the following folders:
- _Msdcs/Dc/_Sites/Default-first-site-name/_Tcp
- _Msdcs/Dc/_Tcp
In these locations, an SRV RR is displayed for the following services:
Q. What is LDAP?
Short for Lightweight Directory Access Protocol,
a set of protocols for accessing information directories. LDAP is based
on the standards contained within the X.500 standard, but is
significantly simpler. And unlike X.500, LDAP supports TCP/IP, which is
necessary for any type of Internet access. Because it’s a simpler
version of X.500, LDAP is sometimes called X.500-lite.
Q. What is FRS (File replication services)?
The File Replication Service (FRS) replicates
specific files using the same multi-master model that Active Directory
uses. It is used by the Distributed File System for replication of DFS
trees that are designated as domain root replicas. It is also used by
Active Directory to synchronize content of the SYSVOL volume
automatically across domain controllers. The reason the FRS service
replicates contents of the SYSVOL folder is so clients will always get a
consistent logon environment when logging on to the domain, no matter
which domain controller actually handles the request. When a client
submits a logon request, he or she submits that request for
authentication to the SYSVOL directory. A subfolder of this directory,
called \scripts, is shared on the network as the netlogon share. Any
logon scripts contained in the netlogon share are processed at logon
time. Therefore, the FRS is responsible for all domain controllers
providing the same logon directory structure to clients throughout the
domain.
Q. Can you connect Active Directory to other 3rd-party Directory Services? Name a few options.
Yes you can Connect Active Directory to other 3rd
-party Directory Services such as dictonaries used by SAP, Domino etc
with the help of MIIS ( Microsoft Identity Integration Server )
you can use dirXML or LDAP to connect to other directories (ie. E-directory from Novell).
Q. Where is the AD database held? What other folders are related to AD?
AD Database is saved in %systemroot%/ntds. You can see other files
also in this folder. These are the main files controlling the AD
structure
- ntds.dit
- edb.log
- res1.log
- res2.log
- edb.chk
When a change is made to the Win2K database,
triggering a write operation, Win2K records the transaction in the log
file (edb.log). Once written to the log file, the change is then written
to the AD database. System performance determines how fast the system
writes the data to the AD database from the log file. Any time the
system is shut down, all transactions are saved to the database.
During the installation of AD, Windows creates two files: res1.log
and res2.log. The initial size of each is 10MB. These files are used to
ensure that changes can be written to disk should the system run out of
free disk space. The checkpoint file (edb.chk) records transactions
committed to the AD database (ntds.dit). During shutdown, a “shutdown”
statement is written to the edb.chk file. Then, during a reboot, AD
determines that all transactions in the edb.log file have been committed
to the AD database. If, for some reason, the edb.chk file doesn’t exist
on reboot or the shutdown statement isn’t present, AD will use the
edb.log file to update the AD database.
The last file in our list of files to know is the AD
database itself, ntds.dit. By default, the file is located in\NTDS,
along with the other files we’ve discussed.
Q. What is the SYSVOL folder?
The SYSVOL folder is critical because it contains the
domain’s public files. This directory is shared out (as SYSVOL), and
any files kept in the SYSVOL folder are replicated to all other domain
controllers in the domain using the File Replication Service (FRS)—and
yes, that’s important to know on the exam.
The SYSVOL folder also contains the following items:
-
The NETLOGON share, which is the location where
domain logon requests are submitted for processing, and where logon
scripts can be stored for client processing at logon time.
-
Windows Group Policies
-
FRS folders and files that must be available and
synchronized between domain controllers if the FRS is in use.
Distributed File System (DFS), for example, uses the FRS to keep shared
data consistent between replicas.
You can go to SYSVOL folder by typing : %systemroot%/sysvol on DC.
Q. Name the AD NCs and replication issues for each NC
*Schema NC, *Configuration NC, * Domain NC
Schema NC: This NC is replicated to
every other domain controller in the forest. It contains information
about the Active Directory schema, which in turn defines the different
object classes and attributes within Active Directory.
Configuration NC: Also replicated to
every other DC in the forest, this NC contains forest-wide
configuration information pertaining to the physical layout of Active
Directory, as well as information about display specifiers and
forest-wide Active Directory quotas.
Domain NC: This NC is replicated to
every other DC within a single Active Directory domain. This is the NC
that contains the most commonly-accessed Active Directory data: the
actual users, groups, computers, and other objects that reside within a
particular Active Directory domain.
Q. What are application partitions? When do I use them?
A1) Application Directory Partition is a partition
space in Active Directory which an application can use to store that
application specific data. This partition is then replicated only to
some specific domain controllers.
The application directory partition can contain any type of data except security principles (users, computers, groups).
**A2) These are specific to Windows Server 2003 domains.
An application directory partition is a directory partition that is
replicated only to specific domain controllers. A domain controller that
participates in the replication of a particular application directory
partition hosts a replica of that partition. Only domain controllers
running Windows Server 2003 can host a replica of an application
directory partition.
Q. How do you create a new application partition?
The DnsCmd command is used to create a new application directory
partition. Ex. to create a partition named “NewPartition” on the domain
controller DC1.contoso.com, log on to the domain controller and type
following command.
DnsCmd DC1/createdirectorypartition NewPartition.contoso.com
Q. How do you view replication properties for AD partitions and DCs?
By using replication monitor
go to start > run > type
replmon
Q. What is the Global Catalog?
The global catalog is the central repository
of information about objects in a tree or forest. By default, a global
catalog is created automatically on the initial domain controller in the
first domain in the forest. A domain controller that holds a copy of
the global catalog is called a global catalog server. You can
designate any domain controller in the forest as a global catalog
server. Active Directory uses multimaster replication to replicate the
global catalog information between global catalog servers in other
domains. It stores a full replica of all object attributes in the
directory for its host domain and a partial replica of all object
attributes contained in the directory for every domain in the forest.
The partial replica stores attributes most frequently used in search
operations (such as a user’s first and last names, logon name, and so
on). Attributes are marked or unmarked for replication in the global
catalog when they are defined in the Active Directory schema. Object
attributes replicated to the global catalog inherit the same permissions
as in source domains, ensuring that data in the global catalog is
secure.
Another Definition of Global Catalog:
Global Catalog Server
A global catalog server is a domain
controller that has an additional duty—it maintains a global catalog. A
global catalog is a master, searchable database that contains
information about every object in every domain in a forest. The global
catalog contains a complete replica of all objects in Active Directory
for its host domain, and contains a partial replica of all objects in
Active Directory for every other domain in the forest.
-
A global catalog server performs two important functions:
-
Provides group membership information during logon and authentication
-
Helps users locate resources in Active Directory
Q. What is schema?
The Active Directory schema defines objects that can be stored in Active Directory. The
schema is
a list of definitions that determines the kinds of objects and the
types of information about those objects that can be stored in Active
Directory. Because the schema definitions themselves are stored as
objects, they can be administered in the same manner as the rest of the
objects in Active Directory. The schema is defined by two types of
objects: schema class objects (also referred to as schema classes) and
schema attribute objects (also referred to as schema attributes).
Q. GC and infrastructure master should not be on same server, why?
Unless your domain consists of only one domain controller, the infrastructure master should not be assigned to a domain controller that’s also a Global Catalog server.
If the infrastructure master and Global Catalog are stored on the same
domain controller, the infrastructure master will not function because
it will never find data that is out of date. It therefore won’t ever
replicate changes to the other domain controllers in the domain. There
are two exceptions:
-
If all your domain controllers are Global Catalog
servers, it won’t matter because all servers will have the latest
changes to the Global Catalog.
-
If you are implementing a single Active Directory
domain, no other domains exist in the forest to keep track of, so in
effect, the infrastructure master is out of a job
Q. Why not make all DCs in a large forest as GCs?
When all the DC become a GC replication traffic will get increased
and we could not keep the Infrastructure master and GC on the same
domain ,so atlease one dc should be act without holding the GC role .
Q. Trying to look at the Schema, how can I do that?
Register the schmmgmt.dll with the command regsvr32
Q. What are the Support Tools? Why do I need them?
Support Tools are the tools that are used for
performing the complicated tasks easily. These can also be the third
party tools. Some of the Support tools include DebugViewer,
DependencyViewer, RegistryMonitor, etc.
Q. What is LDP? What is REPLMON? What is ADSIEDIT? What is NETDOM? What is REPADMIN?
LDP – Label Distribution Protocol
(LDP) is often used to establish MPLS LSPs when traffic engineering is
not required. It establishes LSPs that follow the existing IP routing,
and is particularly well suited for establishing a full mesh of LSPs
between all of the routers on the network.
Replmon – Replmon displays information about Active Directory Replication.
ADSIEDIT – ADSIEdit is a Microsoft
Management Console (MMC) snap-in that acts as a low-level editor for
Active Directory. It is a Graphical User Interface (GUI) tool. Network
administrators can use it for common administrative tasks such as
adding, deleting, and moving objects with a directory service. The
attributes for each object can be edited or deleted by using this tool.
ADSIEdit uses the ADSI application programming interfaces (APIs) to
access Active Directory. The following are the required files for using
this tool: ADSIEDIT.DLL ADSIEDIT.MSC
NETDOM - NETDOM is a command-line
tool that allows management of Windows domains and trust relationships.
It is used for batch management of trusts, joining computers to domains,
verifying trusts, and secure channels.
REPADMIN – REPADMIN is a built-in
Windows diagnostic command-line utility that works at the Active
Directory level. Although specific to Windows, it is also useful for
diagnosing some Exchange replication problems, since Exchange Server is
Active Directory based. REPADMIN doesn’t actually fix replication
problems for you. But, you can use it to help determine the source of a
malfunction.
Q. What are the Naming Conventions used in AD?
Within Active Directory, each object has a name. When
you create an object in Active Directory, such as a user or a computer,
you assign the object a name. This name must be unique within the
domain—you can’t assign an object the same name as any other object
(regardless of its type) in that domain.
At the same time that you create an object, not only
do you assign a name to the object, but Active Directory also assigns
identifiers to the object. Active Directory assigns every object a
globally unique identifier (GUID), and assigns many objects a security
identifier (SID). A GUID is typically a 32-digit hexadecimal number that uniquely identifies an object within Active Directory. A SID is a unique number created by the Windows 2000 Security subsystem that is assigned only to security principal objects (users,
groups, and computers) when they are created.Windows 2000 uses SIDs to
grant or deny a security principal object access to other objects and
network resources.
Active Directory uses a hierarchical naming convention that is based
on Lightweight Directory Access Protocol (LDAP) and DNS standards.
Objects in Active Directory can be referenced by using one of three Active Directory name types:
- Relative distinguished name (RDN)
- Distinguished name (DN)
- User principal name (UPN)
A relative distinguished name (RDN) is the name that is assigned to the object by the administrator when the object is created. For example, when
I create a user named AlanC, the RDN of that user is AlanC. The RDN
only identifies an object—it doesn’t identify the object’s location
within Active Directory. The RDN is the simplest of the three Active
Directory name types, and is sometimes called the common name of the
object.
A distinguished name (DN) consists
of an object’s RDN, plus the object’s location in Active Directory. The
DN supplies the complete path to the object. An object’s DN includes
its RDN, the name of the organizational unit(s) that contains the object
(if any), and the FQDN of the domain. For example, suppose that I
create a user named AlanC in an organizational unit called US in a
domain named Exportsinc.com. The DN of this user would be:
psrjadhav@gmail.com
A user principal name (UPN)
is a shortened version of the DN that is typically used for logon and
e-mail purposes. A UPN consists of the RDN plus the FQDN of the domain.
Using my previous example, the UPN for the user named AlanC would be:
AlanC@Exportsinc.com
Another way you can think of a UPN is as a DN stripped of all organizational unit references.
Q. What are sites? What are they used for?
A site consists of one or more TCP/IP
subnets, which are specified by an administrator. Additionally, if a
site contains more than one subnet, the subnets should be connected by
high-speed, reliable links. Sites do not correspond to domains:You can
have two or more sites within a single domain, or you can have multiple
domains in a single site.A site is solely a grouping based on IP
addresses. Figure 2-7 shows two sites connected by a slow WAN link.

The purpose of sites is to enable servers that
regularly copy data to other servers (such as Active Directory
replication data) to distinguish between servers in their own site
(which are connected by high-speed links) and servers in another site
(which are connected by slower-speed WAN links). Replication between
domain controllers in the same site is fast, and typically
administrators can permit Windows 2000 to automatically perform this
task. Replication between a domain controller in one site and domain
controllers in other sites is slower (because it takes place over a slow
WAN link) and often should be scheduled by the administrator so that
use of network bandwidth for replication is minimized during the
network’s peak-activity hours.
Sites and Active Directory replication can be configured by using Active Directory Sites and Services.
Uses of site:
Sites are primarily used to control replication traffic. Domain
controllers within a site are pretty much free to replicate changes to
the Active Directory database whenever changes are made. Domain
controllers in different sites compress the replication traffic and
operate based on a defined schedule, both of which are intended to cut
down on network traffic.
More specifically, sites are used to control the following:
- Workstation logon traffic
- Replication traffic
- Distributed File System (DFS)
What’s the difference between a site link’s schedule and interval?
Site Link is a physical connection object on which
the replication transport mechanism depends on. Basically to speak it is
the type of communication mechanism used to transfer the data between
different sites. Site Link Schedule is nothing but when the replication
process has to be takes place and the interval is nothing but how many
times the replication has to be takes place in a give time period i.e
Site Link Schedule.
Q. What is replication? How it occurs in AD? What is KCC and ISTG
Each domain controller stores a complete copy of all
Active domain controllers in the same domain. Domain controllers in a
domain automatically replicate directory information for all objects in
the domain to each other. When you perform an action that causes an
update to Active Directory, you are actually making the change at one of
the domain controllers. That domain controller then replicates the
change to all other domain controllers within the domain. You can
control replication of traffic between domain controllers in the network
by specifying how often replication occurs and the amount of data that
each domain controller replicates at one time. Domain controllers
immediately replicate certain important updates, such as the disabling
of a user account.
Active Directory uses multimaster replication, in
which no one domain controller is the master domain controller. Instead,
all domain controllers within a domain are peers, and each domain
controller contains a copy of the directory database that can be written
to. Domain controllers can hold different information for short periods
of time until all domain controllers have synchronized changes to
Active Directory.
Although Active Directory supports multimaster
replication, some changes are impractical to perform in multimaster
fashion. One or more domain controllers can be assigned to perform
single-master replication (operations not permitted to occur at
different places in a network at the same time). Operations master roles are special roles assigned to one or more domain controllers in a domain to perform single-master replication.
Domain controllers detect collisions, which can occur
when an attribute is modified on a domain controller before a change to
the same attribute on another domain controller is completely
propagated. Collisions are detected by comparing each attribute’s
property version number, a number specific to an attribute that is
initialized upon creation of the attribute. Active Directory resolves
the collision by replicating the changed attribute with the higher
property version number.
Q. What can you do to promote a server to DC if you’re in a remote location with slow WAN link?
Install from Media In Windows Server 2003 a
new feature has been added, and this time it’s one that will actually
make our lives easier… You can promote a domain controller using files
backed up from a source domain controller!!!
This feature is called “Install from Media” and it’s
available by running DCPROMO with the /adv switch. It’s not a
replacement for network replication, we still need network connectivity,
but now we can use an old System State copy from another Windows Server
2003, copy it to our future DC, and have the first and basic
replication take place from the media, instead of across the network,
this saving valuable time and network resources.
What you basically have to do is to back up the
systems data of an existing domain controller, restore that backup to
your replica candidate, use DCPromo /Adv to tell it to source from local
media, rather than a network source.
This also works for global catalogs. If we perform a
backup of a global catalog server, then we can create a new global
catalog server by performing DCPromo from that restored media.
IFM Limitations
It only works for the same domain, so you cannot back up a domain
controller in domain A and create a new domain B using that media.
It’s only useful up to the tombstone lifetime with a default of 60
days. So if you have an old backup, then you cannot create a new domain
controller using that, because you’ll run into the problem of
reanimating deleted objects.
Q. How can you forcibly remove AD from a server, and what do you do later?
Demoting Windows Server 2003 DCs:
DCPROMO (Active Directory Installation Wizard) is a toggle switch, which
allows you to either install or remove Active Directory DCs. To
forcibly demote a Windows Server 2003 DC, run the following command
either at the Start, Run, or at the command prompt:
dcpromo /forceremoval
Note: If you’re running
Certificate Services on the DC, you must first remove Certificate
Services before continuing. If you specify the /forceremoval switch on a
server that doesn’t have Active Directory installed, the switch is
ignored and the wizard pretends that you want to install Active
Directory on that server.
Once the wizard starts, you will be prompted for the
Administrator password that you want to assign to the local
administrator in the SAM database. If you have Windows Server 2003
Service Pack 1 installed on the DC, you’ll benefit from a few
enhancements. The wizard will automatically run certain checks and will
prompt you to take appropriate actions. For example, if the DC is a
Global Catalog server or a DNS server, you will be prompted. You will
also be prompted to take an action if your DC is hosting any of the
operations master roles.
Demoting Windows 2000 DCs: On a
Windows 2000 domain controller, forced demotion is supported with
Service Pack 2 and later. The rest of the procedure is similar to the
procedure I described for Windows Server 2003. Just make sure that while
running the wizard, you clear the “This server is the last domain
controller in the domain” check box. On Windows 2000 Servers you won’t
benefit from the enhancements in Windows Server 2003 SP1, so if the DC
you are demoting is a Global Catalog server, you may have to manually
promote some other DC to a Global Catalog server.
Cleaning the Metadata on a Surviving DC : Once
you’ve successfully demoted the DC, your job is not quite done yet. Now
you must clean up the Active Directory metadata. You may be wondering
why I need to clean the metadata manually. The metadata for the demoted
DC is not deleted from the surviving DCs because you forced the
demotion. When you force a demotion, Active Directory basically ignores
other DCs and does its own thing. Because the other DCs are not aware
that you removed the demoted DC from the domain, the references to the
demoted DC need to be removed from the domain.
Although Active Directory has made numerous
improvements over the years, one of the biggest criticisms of Active
Directory is that it doesn’t clean up the mess very well. This is
obvious in most cases but, in other cases, you won’t know it unless you
start digging deep into Active Directory database.
To clean up the metadata you use NTDSUTIL. The
following procedure describes how to clean up metadata on a Windows
Server 2003 SP1. According to Microsoft, the version of NTDSUTIL in SP1
has been enhanced considerably and does a much better job of clean-up,
which obviously means that the earlier versions didn’t do a very good
job. For Windows 2000 DCs, you might want to check out Microsoft
Knowledge Base article 216498, “How to remove data in Active Directory after an unsuccessful domain controller demotion.”
Here’s the step-by-step procedure for cleaning metadata on Windows Server 2003 DCs:
- Logon to the DC as a Domain Administrator.
- At the command prompt, type ntdsutil.
- Type metadata cleanup.
- Type connections.
- Type connect to server servername, where servername is the name of the server you want to connect to.
- Type quit or q to go one level up. You should be at the Metadata Cleanup prompt.
- Type select operation target.
- Type list domains. You will see a list of domains in the forest, each with a different number.
- Type select domain number, where number is the number associated with the domain of your server
- Type list sites.
- Type select site number, where number is the number associated with the site of your server.
- Type list servers in site.
- Type select server number, where number is the number associated with the server you want to remove.
- Type quit to go to Metadata Cleanup prompt.
- Type remove selected server. You should see a confirmation that the removal completed successfully.
- Type quit to exit ntdsutil.
You might also want to cleanup DNS database by deleting all DNS records related to the server.
In general, you will have better luck using forced
promotion on Windows Server 2003, because the naming contexts and other
objects don’t get cleaned as quickly on Windows 2000 Global Catalog
servers, especially servers running Windows 2000 SP3 or earlier. Due to
the nature of forced demotion and the fact that it’s meant to be used
only as a last resort, there are additional things that you should know
about forced demotion.
Even after you’ve used NTDSUTIL to clean the
metadata, you may still need to do additional cleaning manually using
ADSIEdit or other such tools
Q. Can I get user passwords from the AD database?
As of my Knowledge there is no way to extract the password from AD Database. By the way there is a tool called cache dump. Using it we can extract the cached passwords from Windows XP machine which is joined to a Domain.
Q. Name some OU design considerations.
- Design OU structure based on Active Directory business requirements
- NT Resource domains may fold up into OUs
- Create nested OUs to hide objects
- Objects easily moved between OUs
- Departments , Geographic Region, Job Function, Object Type
Q. What is tombstone lifetime attribute?
The number of days before a deleted object is removed from the
directory services. This assists in removing objects from replicated
servers and preventing restores from reintroducing a deleted object.
This value is in the Directory Service object in the configuration NC.
Q. How would you find all users that have not logged on since last month?
If you are using windows 2003 domain environment, then goto Active
Directory Users and Computers, select the Saved Queries, right click it
and select new query, then using the custom common queries and define
query there is one which shows days since last logon
Q. What are the DS* commands?
- DSmod – modifyActiveDirectoryattributes
- DSrm – to delete Active Directory objects
- DSmove - to relocate objects
- DSadd – createnewaccounts
- DSquery- tofindobjectsthatmatchyourqueryattributes
- DSget- listthepropertiesofanobject
What’s the difference between LDIFDE and CSVDE? Usage considerations?
CSVDE is a command that can be used to import and
export objects to and from the AD into a CSV-formatted file. A CSV
(Comma Separated Value) file is a file easily readable in Excel. I will
not go to length into this powerful command, but I will show you some
basic samples of how to import a large number of users into your AD. Of
course, as with the DSADD command, CSVDE can do more than just import
users. Consult your help file for more info. Like CSVDE, LDIFDE is a
command that can be used to import and export objects to and from the AD
into a LDIF-formatted file. A LDIF (LDAP Data Interchange Format) file
is a file easily readable in any text editor; however it is not readable
in programs like Excel. The major difference between CSVDE and LDIFDE
(besides the file format) is the fact that LDIFDE can be used to edit
and delete existing AD objects (not just users), while CSVDE can only
import and export objects
What is DFS?
The Distributed File System is used to build a
hierarchical view of multiple file servers and shares on the network.
Instead of having to think of a specific machine name for each set of
files, the user will only have to remember one name; which will be the
‘key’ to a list of shares found on multiple servers on the network.
Think of it as the home of all file shares with links that point to one
or more servers that actually host those shares.
DFS has the capability of routing a client to the
closest available file server by using Active Directory site metrics. It
can also be installed on a cluster for even better performance and
reliability.
It is important to understand the new concepts that are part of DFS. Below is an definition of each of them.
Dfs root: You can think of this as a share that is visible on the network, and in this share you can have additional files and folders.
Dfs link: A link is another share somewhere on the
network that goes under the root. When a user opens this link they will
be redirected to a shared folder.
Dfs target (or replica): This can be referred to as
either a root or a link. If you have two identical shares, normally
stored on different servers, you can group them together as Dfs Targets
under the same link.
The image below shows the actual folder structure of what the user sees when using DFS and load balancing.

The actual folder structure of DFS and load balancing
Q. What are the types of replication in DFS?
There are two types of replication:
- Automatic – which is only available for Domain DFS
- Manual – which is available for stand alone, DFS and requires all files to be replicated manually.
Q. Which service is responsible for replicating files in SYSVOL folder?
File Replication Service (FRS)
 Networking Essentials
Networking Essentials











![clip_image002[5] clip_image002[5]](http://winadmins.files.wordpress.com/2011/10/clip_image0025_thumb.jpg?w=282&h=190)

![clip_image002[7] clip_image002[7]](http://winadmins.files.wordpress.com/2011/10/clip_image0027_thumb.jpg?w=324&h=120)




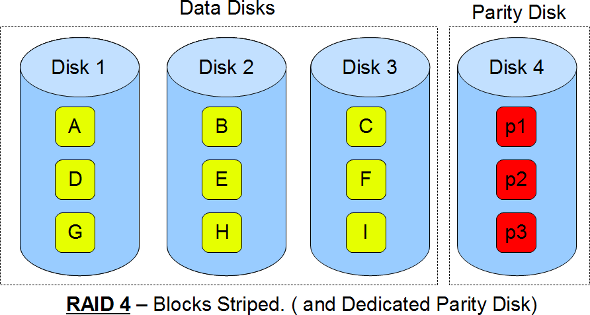
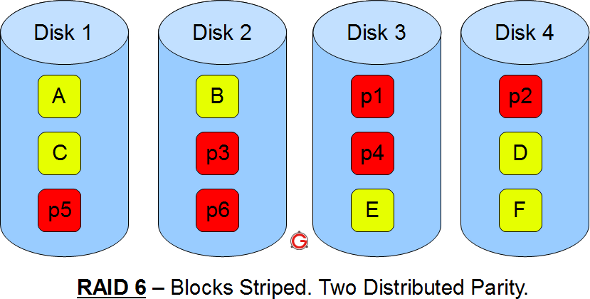
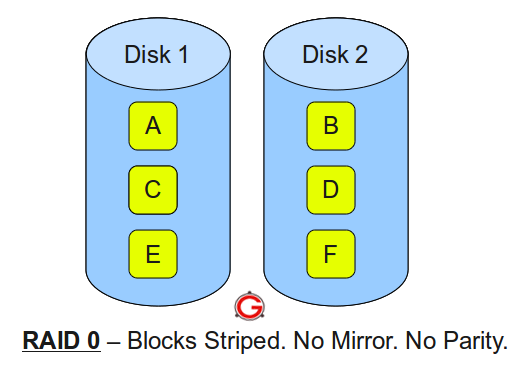
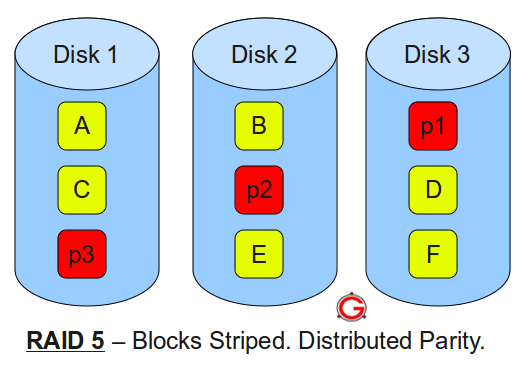
 Following are the key points to remember for RAID level 1.
Following are the key points to remember for RAID level 1.